Amazon ECR (Elastic Container Registry)
🎯 Mục tiêu
Cung cấp nơi lưu trữ Docker image cho backend NestJS monolithic để ECS Fargate có thể kéo image và chạy container. ECR sẽ là registry center cho backend service của VinaShoes e-commerce platform.
🏗️ ECR trong Container Architecture:
- Registry: Central storage cho Docker images
- Immutable Storage: Images không thể bị thay đổi sau khi push
- Integration: Native integration với ECS, Lambda, và các AWS services
- Security: Built-in vulnerability scanning và encryption
📋 Tổng quan kiến trúc
🔑 Các bước triển khai
1. Tạo ECR Repository
Tạo một repository duy nhất để quản lý backend NestJS monolithic service.
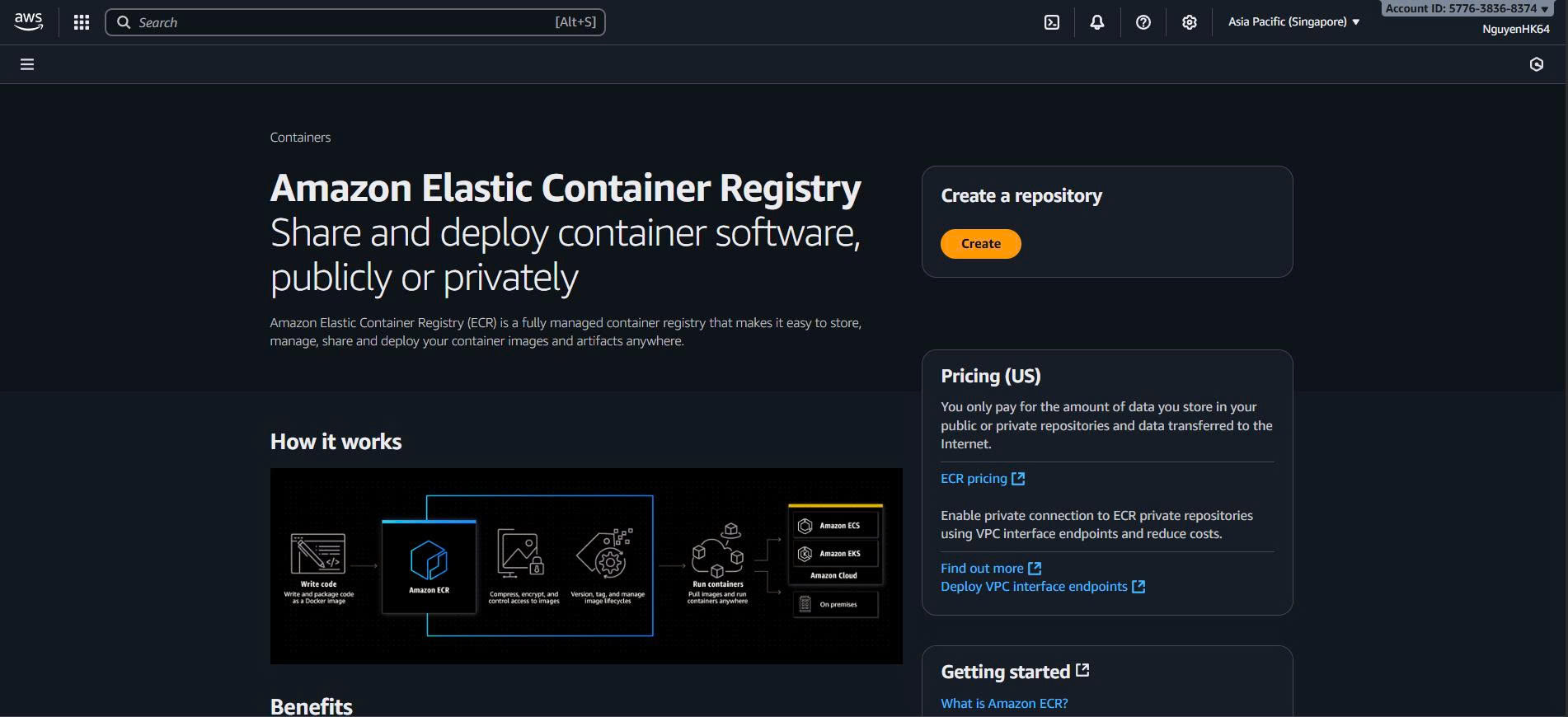
1.1. Truy cập Amazon ECR Console
Console Steps:
Bước 1: Access ECR Service
Console Navigation:
- Login AWS Console:
- Đăng nhập AWS Management Console
- Region: Chọn ap-southeast-1 (Singapore)
- Search “Elastic Container Registry” hoặc “ECR”
📝 CLI Alternative - Quick ECR Access:
# Check ECR service availability in region
aws ecr describe-registry --region ap-southeast-1
# List existing repositories
aws ecr describe-repositories --region ap-southeast-1
# Get ECR usage statistics
aws ecr get-registry-statistics --region ap-southeast-1
- ECR Dashboard Overview:
- View getting started guide
- Check current repositories (nếu có)
- Understand ECR pricing model
1.2. Tạo Repository cho Backend Service
Repository Creation Process:
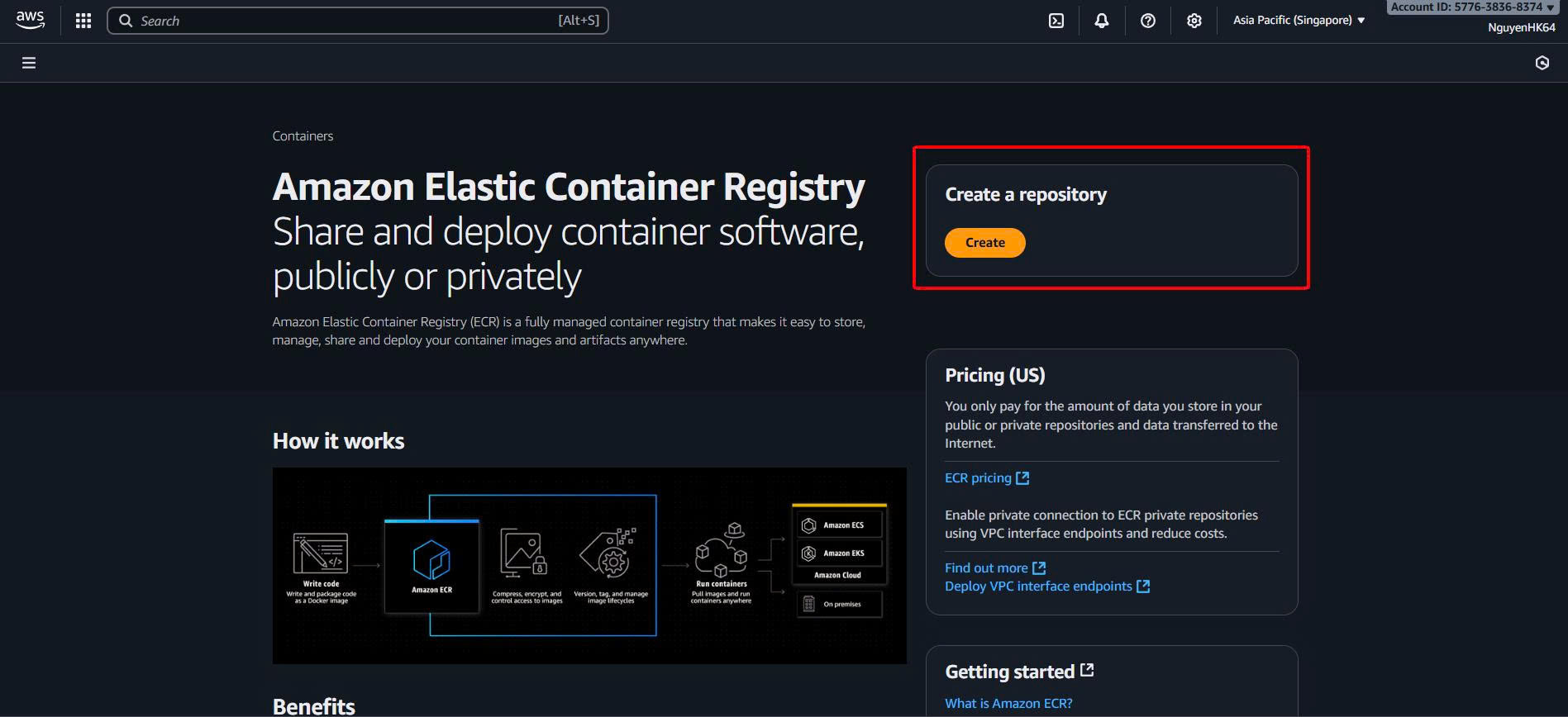
Bước 1: Start Repository Creation
Create Repository:
- Begin Creation Process:
- Click “Create repository” button
- Prepare để setup repository đầu tiên
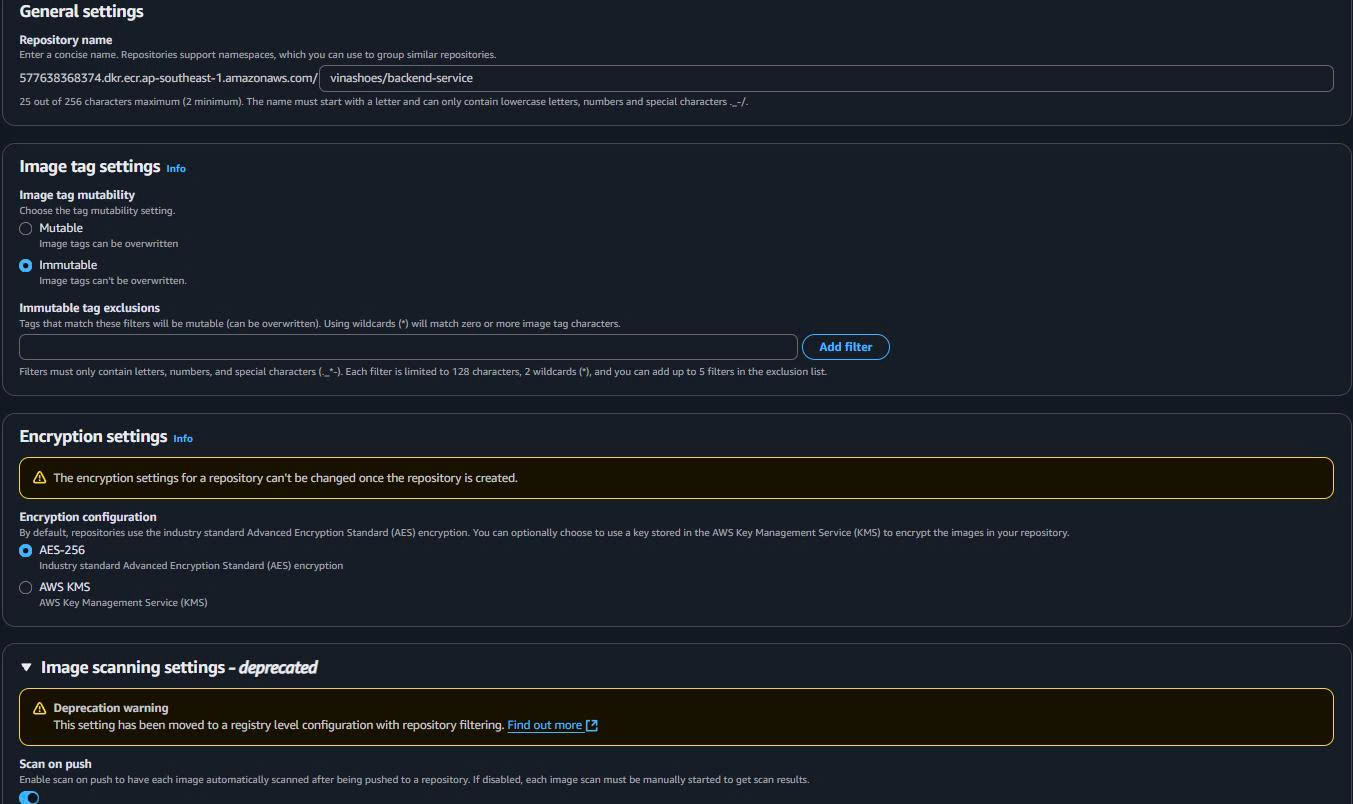
Bước 2: General Settings
Basic Configuration:
- Visibility Settings:
- ☑️ Private (recommended cho production)
- ☐ Public (for open source projects)
- Description: “Private repositories require authentication to access”
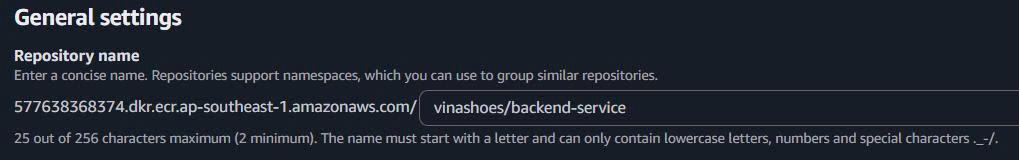
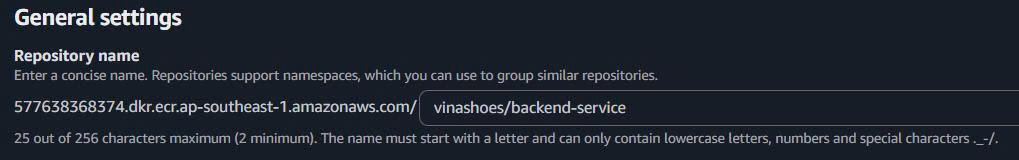
- Repository Name:
- Repository name:
vinashoes/backend-service - Naming convention:
project/service-name - Must be lowercase, can contain hyphens and underscores
- Repository name:
📋 Repository Naming Best Practices:
- Format:
project/service-namehoặcteam/application - Characters: lowercase letters, numbers, hyphens, underscores, forward slashes
- Examples:
vinashoes/backend-service,frontend/web-app,shared/nginx - Organization: Group related services với common prefix
Bước 3: Tag Immutability
Tag Settings:
- Tag Immutability:
- ☑️ Enabled (recommended for production)
- ☐ Disabled (allows tag overwriting)
- Description: “Prevents image tags from being overwritten”
⚠️ Tag Immutability Impact:
- Enabled: Tags cannot be overwritten, ensures image consistency
- Disabled: Allows
latesttag updates, more flexible but less secure - Best Practice: Enable cho production environments
- Development: Có thể disable cho development repositories với frequent updates
Bước 4: Image Scanning
Security Scanning:
- Scan on Push:
- ☑️ Enabled (recommended for security)
- Scan type: Basic scanning (free tier)
- Description: “Automatically scan for vulnerabilities when images are pushed”
- Enhanced Scanning (Optional):
- Available for additional cost
- Provides more detailed vulnerability information
- Includes OS and programming language vulnerabilities
🔍 Security Scanning Types:
- Basic Scanning: Free, focuses on CVE database
- Enhanced Scanning: Paid, includes OS packages, language libraries
- Manual Scans: Can trigger on-demand scans
- Continuous Scanning: Automatically rescans khi new vulnerabilities discovered
📝 CLI - Configure Scanning:
# Enable scanning on existing repository
aws ecr put-image-scanning-configuration \
--repository-name vinashoes/backend-service \
--image-scanning-configuration scanOnPush=true \
--region ap-southeast-1
# Start manual scan
aws ecr start-image-scan \
--repository-name vinashoes/backend-service \
--image-id imageTag=latest \
--region ap-southeast-1
Bước 5: Encryption Settings
Data Encryption:
- Encryption Configuration:
- ☑️ AES-256 (default, recommended)
- ☐ KMS (for advanced key management)
- Description: “Server-side encryption for stored images”
🔐 Encryption Options:
- AES-256: Server-side encryption với AWS managed keys (default)
- KMS: Customer managed keys cho advanced control
- Cost: AES-256 free, KMS có additional charges
- Use Cases: KMS cho compliance requirements, AES-256 cho general use
Bước 6: Create Repository
Finalize Creation:
- Review Settings:
- Verify repository name
- Confirm visibility and security settings
- Check encryption configuration
- Create Repository:
- Click “Create repository”
- Wait for creation process (1-2 minutes)
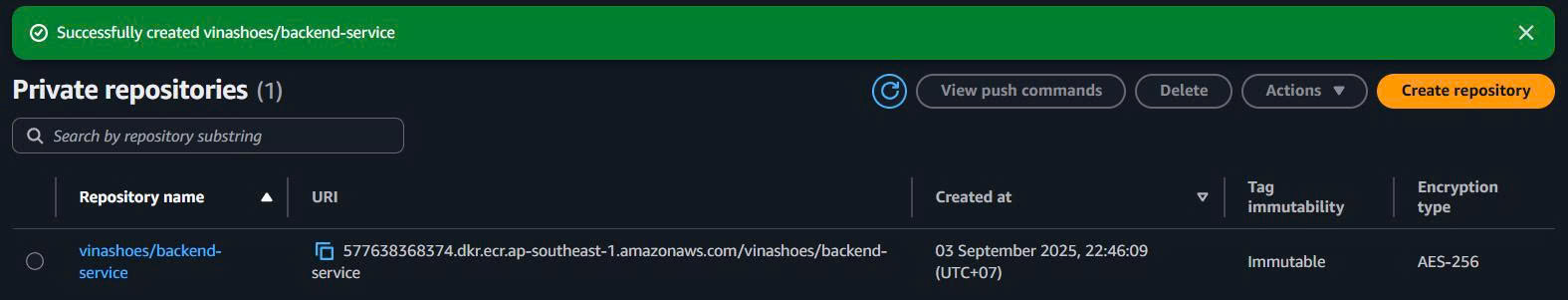
AWS CLI Alternative (để tạo nhanh):
# Create backend service repository
aws ecr create-repository \
--repository-name vinashoes/backend-service \
--image-tag-mutability IMMUTABLE \
--image-scanning-configuration scanOnPush=true \
--region ap-southeast-1
📝 CLI - Advanced Repository Creation:
# Create repository với KMS encryption
aws ecr create-repository \
--repository-name vinashoes/backend-service \
--image-tag-mutability IMMUTABLE \
--image-scanning-configuration scanOnPush=true \
--encryption-configuration encryptionType=KMS,kmsKey=alias/ecr-key \
--region ap-southeast-1
# Verify repository creation
aws ecr describe-repositories \
--repository-names vinashoes/backend-service \
--region ap-southeast-1
# Get repository URI
aws ecr describe-repositories \
--repository-names vinashoes/backend-service \
--query 'repositories[0].repositoryUri' \
--output text \
--region ap-southeast-1
2. Thiết lập Lifecycle Policy
Lifecycle Policy giúp tự động xóa images cũ để tiết kiệm chi phí storage.
💰 Cost Management Importance:
- ECR charges $0.10 per GB-month cho stored images
- Untagged images từ failed builds có thể accumulate quickly
- Production images cũ có thể consume significant storage
- Lifecycle policies essential cho cost optimization
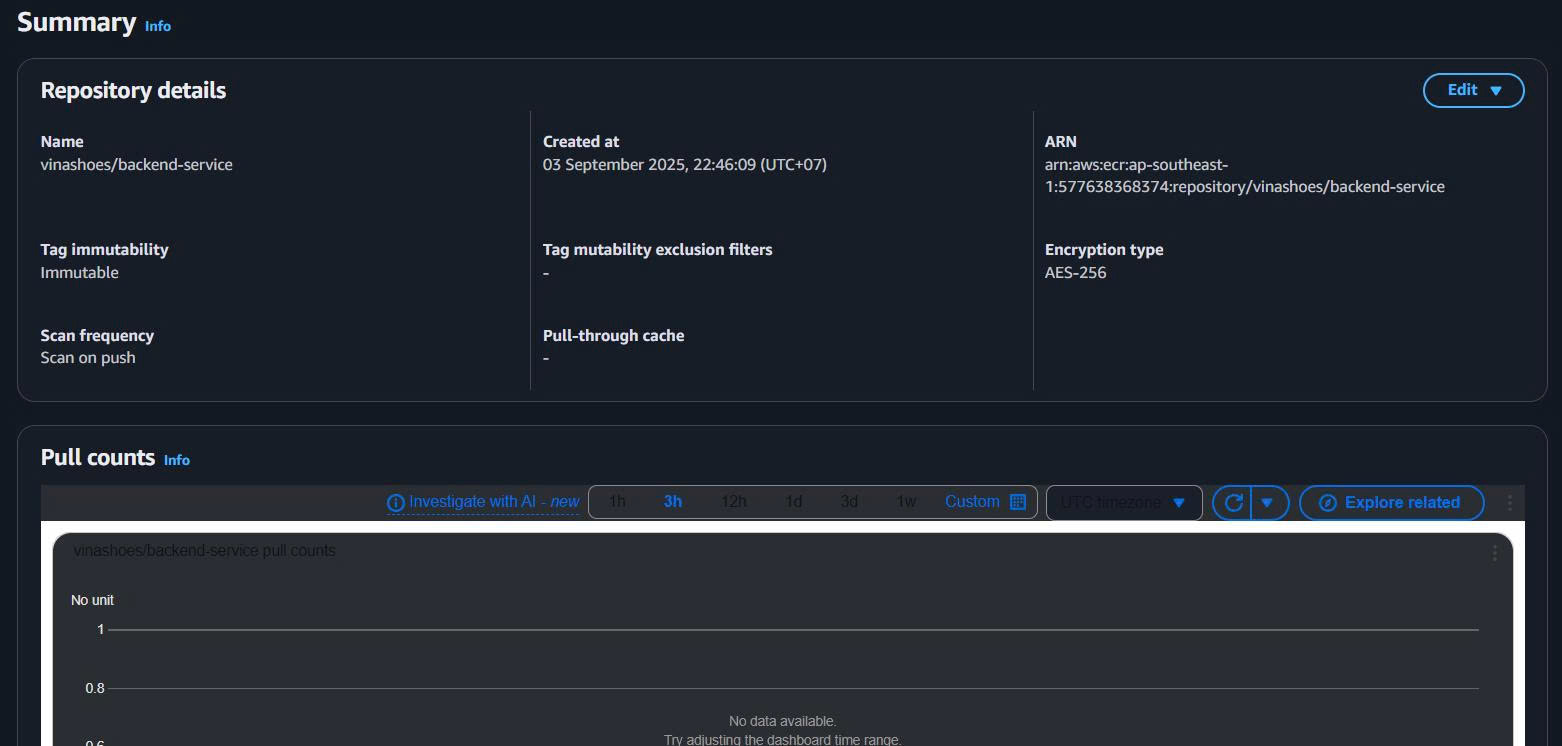
2.1. Configure Lifecycle Policy cho Backend Service
Console Steps:
Bước 1: Access Repository Settings
Repository Management:
- Navigate to Repository:
- Từ ECR Console → Click vào
vinashoes/backend-service - Repository detail page sẽ mở
- Từ ECR Console → Click vào
- Lifecycle Policy Tab:
- Click tab “Lifecycle Policy”
- Hiện tại sẽ không có policy nào
Bước 2: Create Lifecycle Rules
Policy Configuration:
-
Start Policy Creation:
- Click “Create rule”
- Policy editor sẽ mở
-
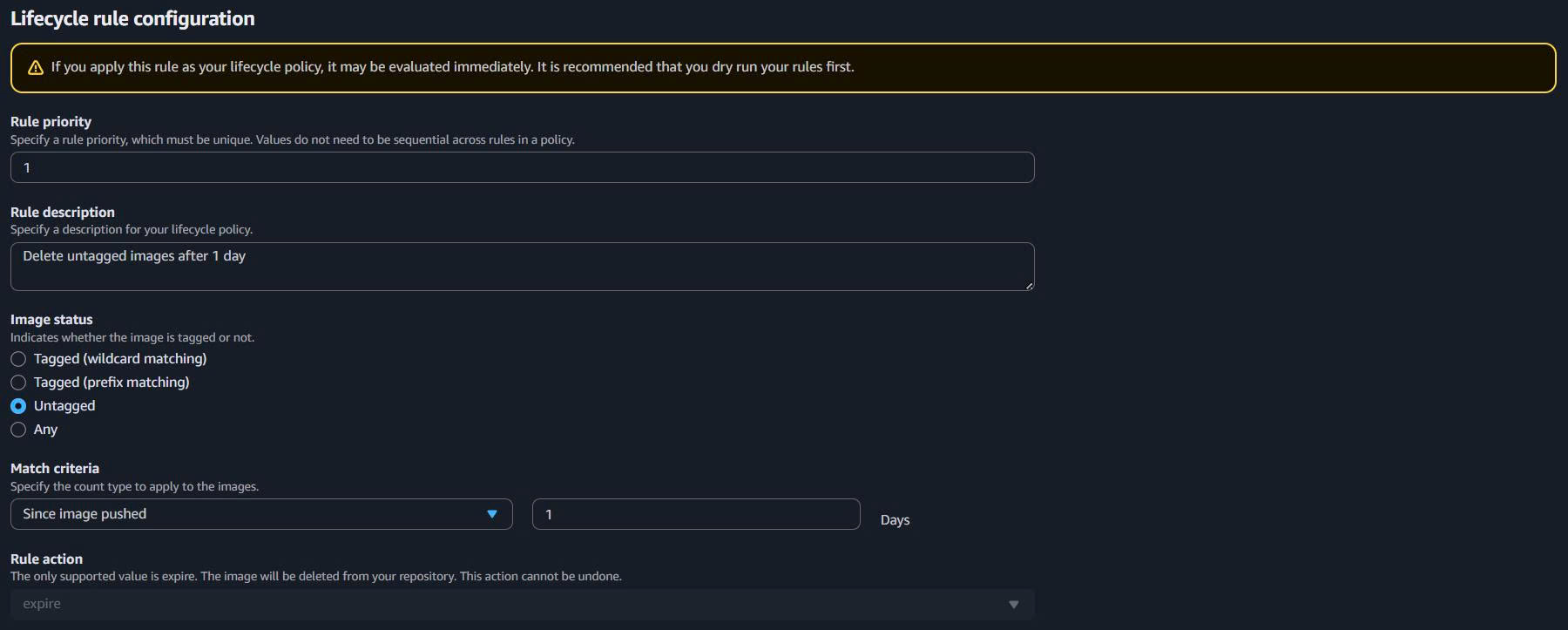
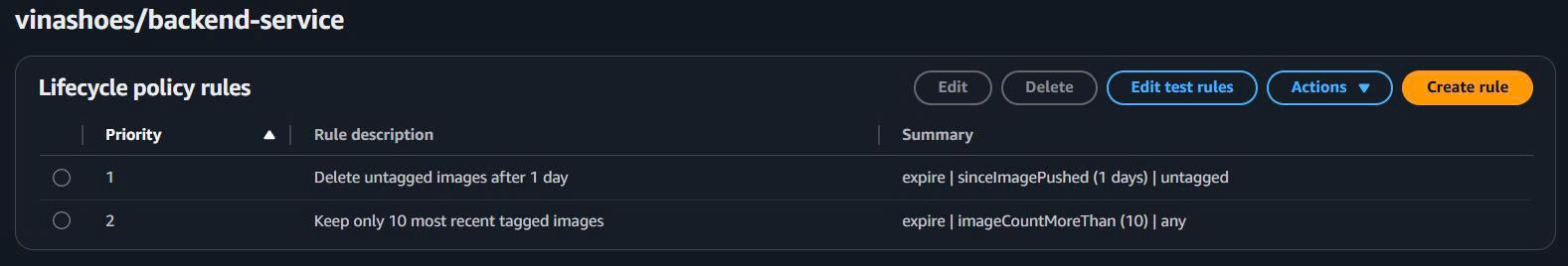
Rule 1: Delete Untagged Images
- Rule priority:
1 - Rule description:
Delete untagged images after 1 day - Image status: Untagged
- Since image pushed:
1days
- Rule priority:
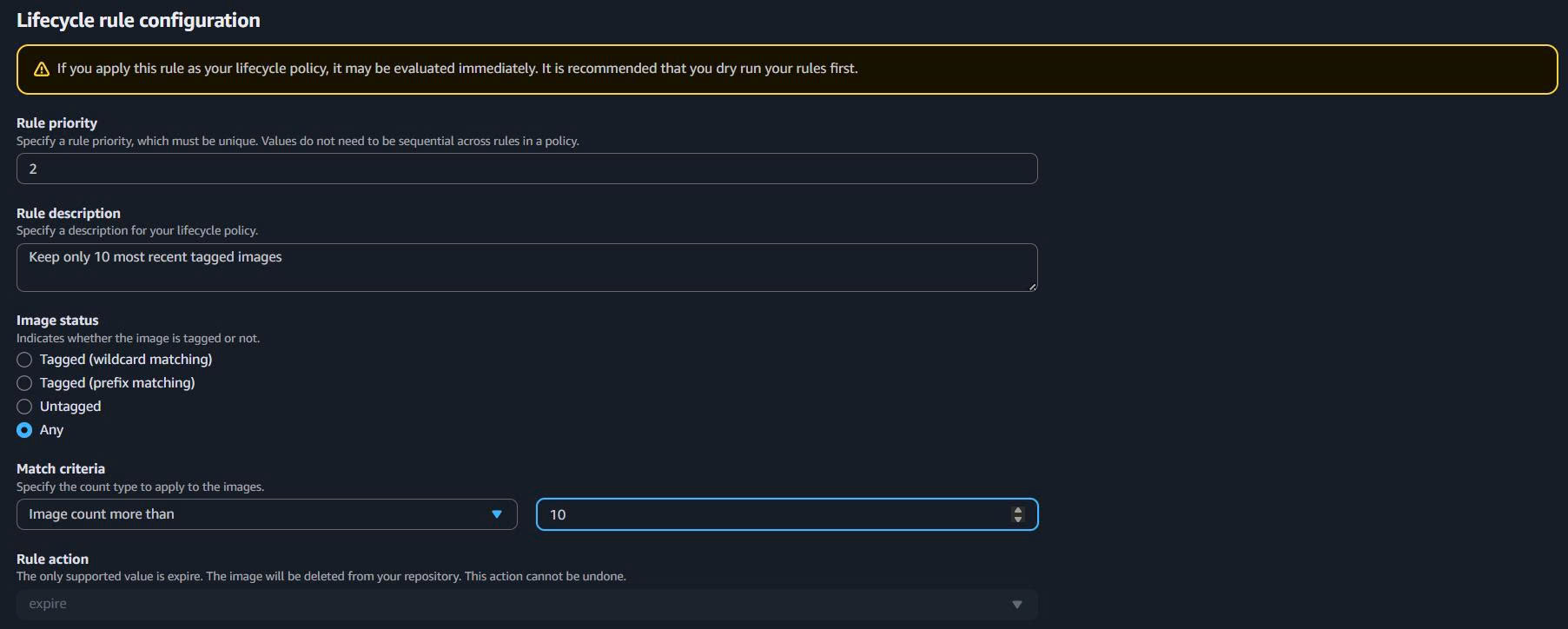
- Rule 2: Keep Recent Tagged Images
- Rule priority:
2 - Rule description:
Keep only 10 most recent tagged images - Image status: Tagged
- Tag status: Any
- Count type: Image count more than:
10
- Rule priority:
Bước 3: Save Lifecycle Policy
Policy Finalization:
-
Review Rules:
- Verify both rules configuration
- Check priority order
- Ensure logic is correct
-
Save Policy:
- Click “Save”
- Policy sẽ active ngay lập tức
- Policy applies cho future pushes
📝 CLI - Advanced Lifecycle Policies:
# Create comprehensive lifecycle policy
cat > lifecycle-policy.json << EOF
{
"rules": [
{
"rulePriority": 1,
"description": "Keep only 1 untagged image",
"selection": {
"tagStatus": "untagged",
"countType": "imageCountMoreThan",
"countNumber": 1
},
"action": {
"type": "expire"
}
},
{
"rulePriority": 2,
"description": "Keep last 10 production images",
"selection": {
"tagStatus": "tagged",
"tagPrefixList": ["v", "prod"],
"countType": "imageCountMoreThan",
"countNumber": 10
},
"action": {
"type": "expire"
}
},
{
"rulePriority": 3,
"description": "Delete dev images older than 7 days",
"selection": {
"tagStatus": "tagged",
"tagPrefixList": ["dev", "feature"],
"countType": "sinceImagePushed",
"countUnit": "days",
"countNumber": 7
},
"action": {
"type": "expire"
}
}
]
}
EOF
# Apply lifecycle policy
aws ecr put-lifecycle-policy \
--repository-name vinashoes/backend-service \
--lifecycle-policy-text file://lifecycle-policy.json \
--region ap-southeast-1
# Preview lifecycle policy actions
aws ecr preview-lifecycle-policy \
--repository-name vinashoes/backend-service \
--lifecycle-policy-text file://lifecycle-policy.json \
--region ap-southeast-1
3. Build & Push Docker Image
3.1. Chuẩn bị Docker Image cho NestJS Monolithic
Development Setup:
Bước 1: Tạo Dockerfile cho Backend Service
Dockerfile Configuration:
Dockerfile cho Backend Service:
# Multi-stage build for optimization
FROM node:18-alpine AS builder
# Set working directory
WORKDIR /app
# Copy package files first (for better caching)
COPY package*.json ./
COPY tsconfig*.json ./
# Install dependencies
RUN npm ci --only=production && npm cache clean --force
# Copy source code
COPY src/ ./src/
# Build the application
RUN npm run build
# Production stage
FROM node:18-alpine AS production
# Set working directory
WORKDIR /app
# Create non-root user for security
RUN addgroup -g 1001 -S nodejs && \
adduser -S nestjs -u 1001
# Copy built application from builder stage
COPY --from=builder --chown=nestjs:nodejs /app/dist ./dist
COPY --from=builder --chown=nestjs:nodejs /app/node_modules ./node_modules
COPY --chown=nestjs:nodejs package*.json ./
# Switch to non-root user
USER nestjs
# Expose application port
EXPOSE 3000
# Add health check
HEALTHCHECK --interval=30s --timeout=3s --start-period=5s --retries=3 \
CMD curl -f http://localhost:3000/health || exit 1
# Start the application
CMD ["node", "dist/main.js"]
🏗️ Multi-stage Build Benefits:
- Smaller Images: Only production files in final image
- Security: No development tools in production image
- Performance: Faster container startup times
- Best Practice: Separate build và runtime environments
Create .dockerignore:
# Dependencies
node_modules
# Logs
npm-debug.log*
yarn-debug.log*
yarn-error.log*
# Build output
dist
# Environment files
.env
.env.local
.env.production
# Git
.git
.gitignore
# IDE
.vscode
.idea
# OS generated files
.DS_Store
Thumbs.db
# Coverage reports
coverage
.nyc_output
# Testing
.cache
📦 Docker Build Optimization:
# Build với BuildKit cho faster builds
DOCKER_BUILDKIT=1 docker build -t vinashoes/backend-service:latest .
# Build với build arguments
docker build \
--build-arg NODE_ENV=production \
--build-arg API_VERSION=v1.0.0 \
-t vinashoes/backend-service:v1.0.0 .
# Multi-platform build
docker buildx build \
--platform linux/amd64,linux/arm64 \
-t vinashoes/backend-service:latest .
# Build với cache mount
docker build \
--mount=type=cache,target=/root/.npm \
-t vinashoes/backend-service:latest .
Bước 2: Build Image Locally
Local Build Process:
Build Backend Service:
# Navigate to Backend Service directory
cd backend-service
# Build Docker image với multiple tags
docker build -t vinashoes/backend-service:latest .
docker build -t vinashoes/backend-service:v1.0.0 .
# Verify image was created
docker images | grep vinashoes/backend-service
Test Image Locally:
# Test Backend Service container
docker run -d -p 3000:3000 --name test-backend vinashoes/backend-service:latest
# Test health endpoint
curl http://localhost:3000/health
# Test API endpoints
curl http://localhost:3000/api/users
curl http://localhost:3000/api/products
curl http://localhost:3000/api/orders
# Check logs
docker logs test-backend
# Cleanup
docker stop test-backend && docker rm test-backend
🔍 Local Testing Best Practices:
- Health Checks: Always test health endpoints before pushing
- Port Conflicts: Check no other services using port 3000
- Environment Variables: Test với realistic environment settings
- Resource Limits: Monitor memory và CPU usage during testing
- Log Output: Verify logging works correctly
3.2. Configure AWS CLI và Docker Authentication
Authentication Setup:
Bước 1: AWS CLI Configuration
AWS CLI Setup:
# Configure AWS CLI (if not already done)
aws configure
# AWS Access Key ID: [Your Access Key]
# AWS Secret Access Key: [Your Secret Key]
# Default region name: ap-southeast-1
# Default output format: json
# Verify AWS CLI is working
aws sts get-caller-identity
📝 AWS CLI Advanced Configuration:
# Configure multiple profiles
aws configure --profile production
aws configure --profile development
# Use specific profile
aws ecr describe-repositories --profile production --region ap-southeast-1
# Configure with environment variables
export AWS_ACCESS_KEY_ID=your-access-key
export AWS_SECRET_ACCESS_KEY=your-secret-key
export AWS_DEFAULT_REGION=ap-southeast-1
# Verify permissions
aws iam get-user
aws sts get-caller-identity
# Check ECR permissions specifically
aws ecr describe-registry --region ap-southeast-1
Bước 2: Docker Login to ECR
ECR Authentication:
Console Method:
- Get Login Command:
- Vào ECR Console → Click vào repository
- Click “View push commands”
- Copy login command
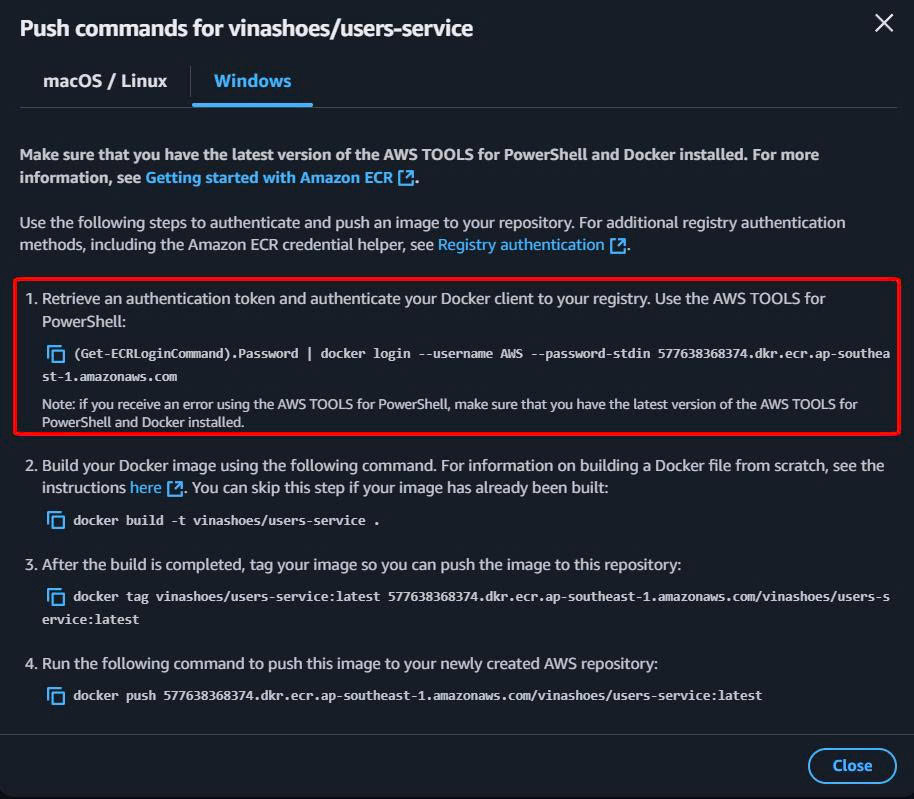
CLI Method:
# Get ECR login token và authenticate Docker
aws ecr get-login-password --region ap-southeast-1 | \
docker login --username AWS --password-stdin <account-id>.dkr.ecr.ap-southeast-1.amazonaws.com
# Verify login successful
echo "Login Succeeded"
🔐 ECR Authentication Important Notes:
- Token Expiry: ECR login tokens expire after 12 hours
- Region Specific: Login required per region
- Account Specific: Cannot access other AWS accounts without cross-account policies
- Docker Daemon: Must have Docker daemon running before login
📝 CLI - Authentication Troubleshooting:
# Check if Docker is running
docker version
# Clear Docker credentials
docker logout <account-id>.dkr.ecr.ap-southeast-1.amazonaws.com
# Re-authenticate với detailed output
aws ecr get-login-password --region ap-southeast-1 | \
docker login --username AWS --password-stdin \
<account-id>.dkr.ecr.ap-southeast-1.amazonaws.com
# Test authentication
docker pull alpine:latest
docker tag alpine:latest <account-id>.dkr.ecr.ap-southeast-1.amazonaws.com/test:latest
3.3. Tag và Push Image lên ECR
Image Push Process:
Bước 1: Get ECR Repository URIs
Repository Information:
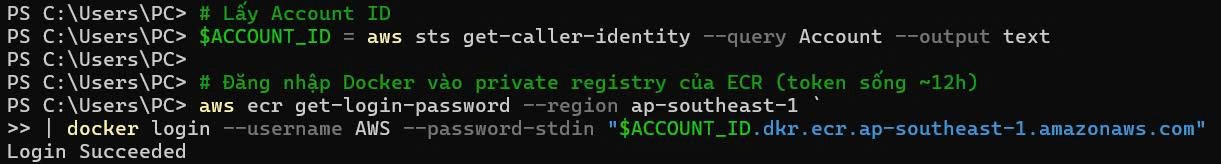
# Get AWS Account ID
export AWS_ACCOUNT_ID=$(aws sts get-caller-identity --query Account --output text)
# Set ECR registry URL
export ECR_REGISTRY=${AWS_ACCOUNT_ID}.dkr.ecr.ap-southeast-1.amazonaws.com
echo "ECR Registry: $ECR_REGISTRY"
🏷️ Image Tagging Strategies:
- Latest: Always points to most recent build
- Version Tags: Semantic versioning (v1.0.0, v1.1.0)
- Git Hash: Short commit hash cho traceability
- Environment: dev, staging, prod prefixes
- Date: Build date cho temporal tracking
📝 CLI - Advanced Tagging:
# Get current git commit hash
export GIT_HASH=$(git rev-parse --short HEAD)
export BUILD_DATE=$(date +%Y%m%d)
# Tag với multiple strategies
docker tag vinashoes/backend-service:latest \
${ECR_REGISTRY}/vinashoes/backend-service:latest
docker tag vinashoes/backend-service:latest \
${ECR_REGISTRY}/vinashoes/backend-service:${GIT_HASH}
docker tag vinashoes/backend-service:latest \
${ECR_REGISTRY}/vinashoes/backend-service:${BUILD_DATE}
docker tag vinashoes/backend-service:latest \
${ECR_REGISTRY}/vinashoes/backend-service:prod-${BUILD_DATE}
Bước 2: Tag Image với ECR URI
Image Tagging:
Tag Backend Service:
# Tag local image với ECR repository URL
docker tag vinashoes/backend-service:latest \
${ECR_REGISTRY}/vinashoes/backend-service:latest
docker tag vinashoes/backend-service:v1.0.0 \
${ECR_REGISTRY}/vinashoes/backend-service:v1.0.0
Bước 3: Push Image to ECR
Push Process:
Push Backend Service:
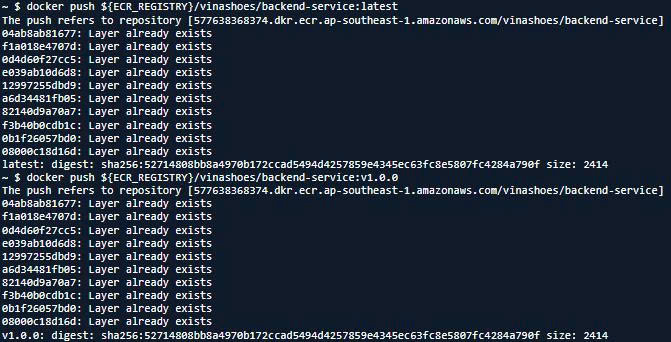
# Push both tags
docker push ${ECR_REGISTRY}/vinashoes/backend-service:latest
docker push ${ECR_REGISTRY}/vinashoes/backend-service:v1.0.0
🚀 Push Optimization:
# Push với parallel uploads (faster)
docker push --all-tags ${ECR_REGISTRY}/vinashoes/backend-service
# Monitor push progress
docker push ${ECR_REGISTRY}/vinashoes/backend-service:latest 2>&1 | \
grep -E "(Pushed|Layer already exists)"
# Verify push success
aws ecr list-images \
--repository-name vinashoes/backend-service \
--region ap-southeast-1
# Get image digest
aws ecr batch-get-image \
--repository-name vinashoes/backend-service \
--image-ids imageTag=latest \
--query 'images[0].imageManifest' \
--output text | sha256sum
Bước 4: Verify Image trong ECR Console
Console Verification:
- Check Repository Contents:
- Vào ECR Console → Click vào repository
- Verify image appears với correct tags
- Check image size và push timestamps
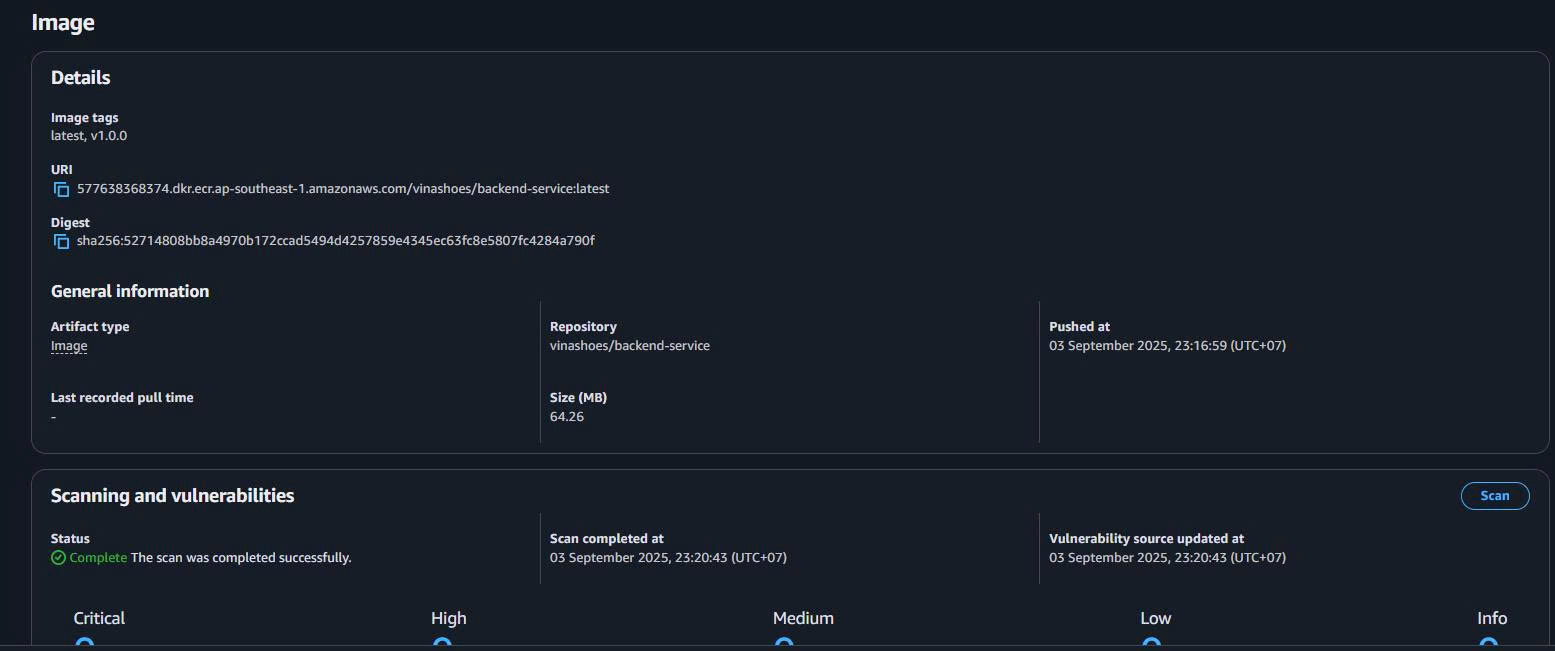
- View Image Details:
- Click vào image tag để xem chi tiết
- Check image manifest
- Review vulnerability scan results
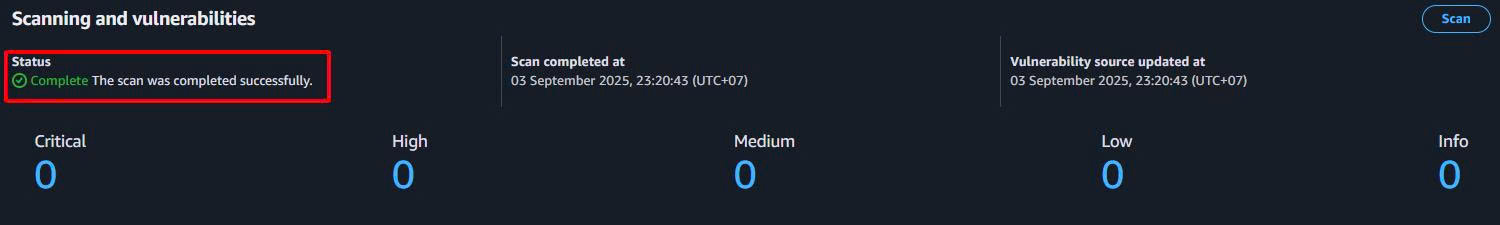
4. Security Scanning Results
4.1. Review Vulnerability Scan Results
Security Assessment:
Bước 1: Access Scan Results
Scan Results Review:
- Navigate to Scan Results:
- Vào ECR Console → Repository → Click vào image tag
- Tab “Vulnerabilities” → Review scan findings
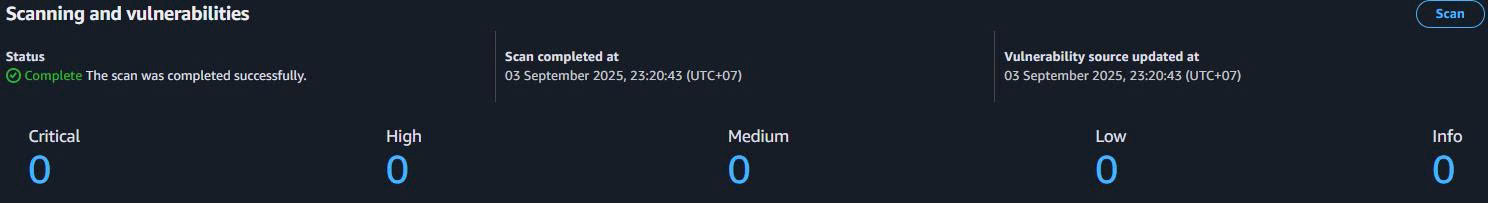
- Vulnerability Details:
- Critical: Immediate action required
- High: Should be addressed soon
- Medium: Address in next update cycle
- Low: Monitor và address when convenient
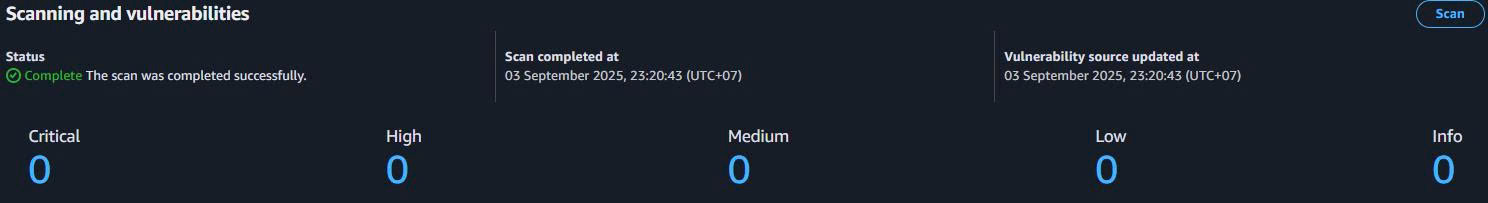
Bước 2: Vulnerability Remediation
Security Actions:
-
Review Critical Vulnerabilities:
- Check if vulnerabilities affect your application
- Review CVE details và severity
- Plan remediation strategy
-
Common Remediation Steps:
- Update base image (node:18-alpine → node:20-alpine)
- Update package dependencies
- Apply security patches
- Rebuild và re-push images
CLI Method to check scans:
# Check scan results for specific image
aws ecr describe-image-scan-findings \
--repository-name vinashoes/backend-service \
--image-id imageTag=v1.0.0 \
--region ap-southeast-1
5. IAM Permissions Setup
5.1. Create ECS Execution Role
IAM Configuration cho ECR Access:
Bước 1: Create ECS Task Execution Role
Console Steps:
- Access IAM Console:
- Vào AWS Console → Search “IAM”
- Navigate to Roles → Create role
- Role Configuration:
- Trusted entity type: AWS service
- Service: Elastic Container Service
- Use case: Elastic Container Service Task
Bước 2: Attach Policies
Policy Attachment:
- Required Policies:
- ☑️
AmazonECSTaskExecutionRolePolicy(managed policy) - ☑️
AmazonEC2ContainerRegistryReadOnly(managed policy)
- ☑️
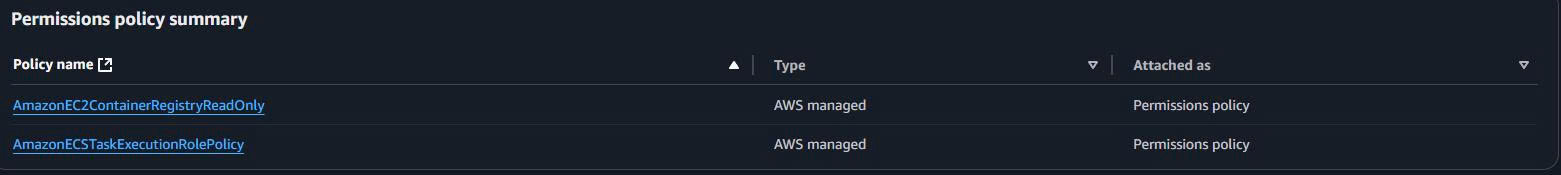
- Role Details:
- Role name:
ecsTaskExecutionRole - Description: “Allows ECS tasks to pull images from ECR and send logs to CloudWatch”
- Role name:
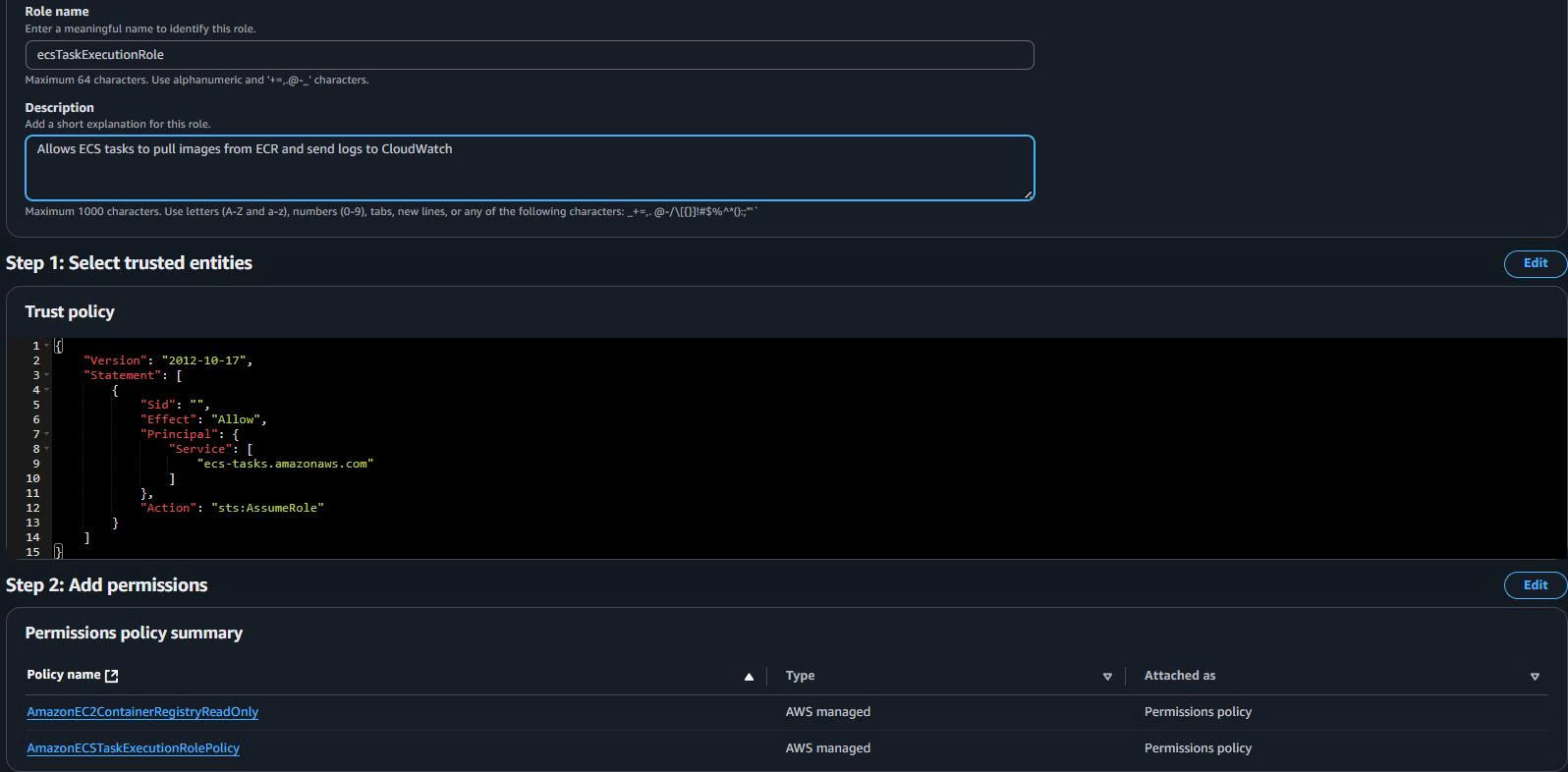
CLI Alternative:
# Create trust policy document
cat > ecs-trust-policy.json << EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ecs-tasks.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
EOF
# Create IAM role
aws iam create-role \
--role-name ecsTaskExecutionRole \
--assume-role-policy-document file://ecs-trust-policy.json
# Attach managed policies
aws iam attach-role-policy \
--role-name ecsTaskExecutionRole \
--policy-arn arn:aws:iam::aws:policy/service-role/AmazonECSTaskExecutionRolePolicy
aws iam attach-role-policy \
--role-name ecsTaskExecutionRole \
--policy-arn arn:aws:iam::aws:policy/AmazonEC2ContainerRegistryReadOnly
5.2. Verify ECR Permissions
Permission Testing:
Test ECR Access
Permission Verification:
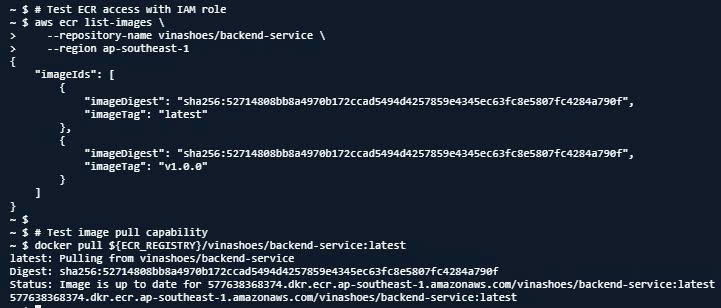
# Test ECR access with IAM role
aws ecr list-images \
--repository-name vinashoes/backend-service \
--region ap-southeast-1
# Test image pull capability
docker pull ${ECR_REGISTRY}/vinashoes/backend-service:latest
6. Testing & Validation
6.1. Image Pull Testing
Functionality Testing:
Bước 1: Test Image Pull
Pull Test:
# Clean local images first
docker rmi ${ECR_REGISTRY}/vinashoes/backend-service:latest
# Test pull from ECR
docker pull ${ECR_REGISTRY}/vinashoes/backend-service:latest
# Verify image pulled successfully
docker images | grep vinashoes
Bước 2: Test Container Functionality
Container Test:
# Run container from ECR image
docker run -d -p 3000:3000 --name test-ecr-backend \
${ECR_REGISTRY}/vinashoes/backend-service:latest
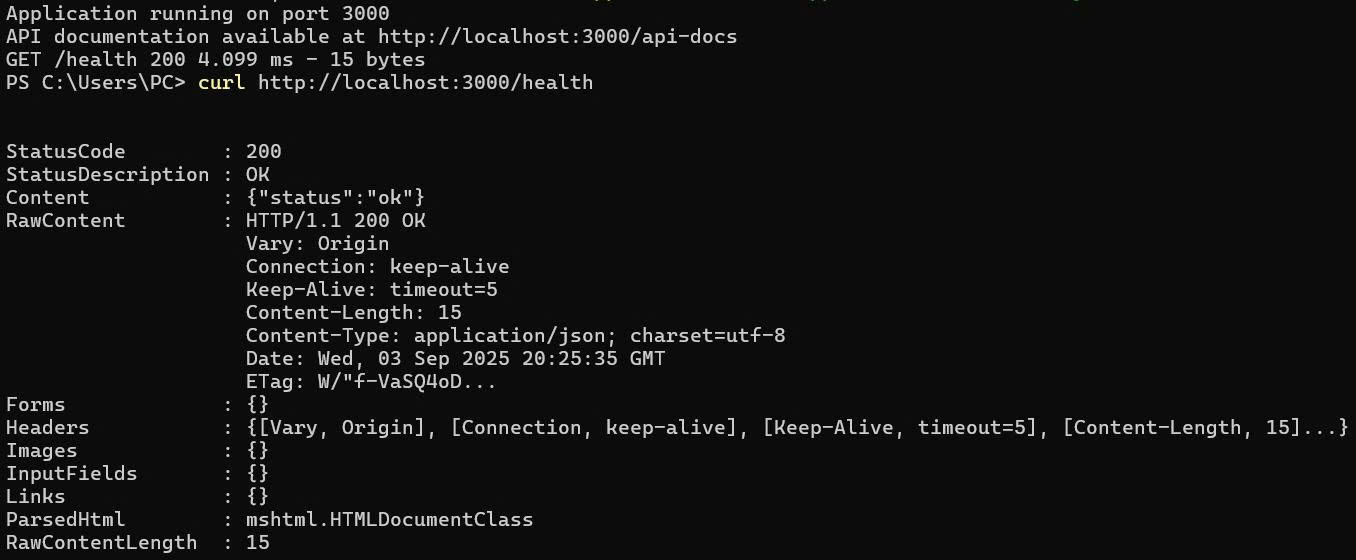
# Test application health
curl http://localhost:3000/health
# Test API endpoints
curl http://localhost:3000/api/users
curl http://localhost:3000/api/products
curl http://localhost:3000/api/orders
# Check container logs
docker logs test-ecr-backend
# Cleanup
docker stop test-ecr-backend && docker rm test-ecr-backend
6.2. Final Verification
Complete System Check:
Repository Status Summary
Verification Checklist:
- ✅ Repository created successfully
- ✅ Image pushed với proper tags (latest, v1.0.0)
- ✅ Lifecycle policy configured
- ✅ Security scanning completed
- ✅ IAM permissions setup
- ✅ Pull/run testing successful
Deliverables
📦 ECR Repository Created:
vinashoes/backend-service(single repository cho monolithic backend)
🏷️ Docker Image:
- Backend service image với tags:
latestvàv1.0.0 - Image tested locally trước khi push
- Multi-stage build được optimized cho production
- Chứa tất cả modules: Users, Products, Orders, Cart, Payment
🔒 Security & Compliance:
- Image vulnerability scanning enabled và completed
- Lifecycle policy configured cho cost optimization
- Private repository với proper access controls
- Encryption at rest với AES-256
🔍 Security Validation CLI:
# Check scan status and results
aws ecr describe-image-scan-findings \
--repository-name vinashoes/backend-service \
--image-id imageTag=latest \
--region ap-southeast-1
# Get security findings summary
aws ecr describe-image-scan-findings \
--repository-name vinashoes/backend-service \
--image-id imageTag=latest \
--query 'imageScanFindingsSummary.findingCounts' \
--region ap-southeast-1
# Check image encryption status
aws ecr describe-repositories \
--repository-names vinashoes/backend-service \
--query 'repositories[0].encryptionConfiguration' \
--region ap-southeast-1
🔑 IAM Permissions:
- ECS Task Execution Role với ECR read permissions
- Proper policies attached cho container pulls
- Verified ECR access functionality
🛡️ IAM Permission Validation:
# Test ECR access with current credentials
aws ecr describe-repositories --region ap-southeast-1
# Check specific repository permissions
aws ecr describe-repository-permissions \
--repository-name vinashoes/backend-service \
--region ap-southeast-1
# Test image pull permissions
aws ecr batch-get-image \
--repository-name vinashoes/backend-service \
--image-ids imageTag=latest \
--region ap-southeast-1
# Validate task execution role
aws iam get-role \
--role-name ecsTaskExecutionRole \
--query 'Role.AssumeRolePolicyDocument'
🧪 Testing Results:
- Image push successful
- Image pull testing completed
- Container functionality verified
- Health checks và API endpoints working properly
🧪 Production Testing Checklist:
# Test image pull from different environments
docker pull ${ECR_REGISTRY}/vinashoes/backend-service:latest
# Verify image integrity
docker inspect ${ECR_REGISTRY}/vinashoes/backend-service:latest \
--format='{{.Id}}'
# Test container startup and health
docker run -d --name test-backend \
-p 3000:3000 \
${ECR_REGISTRY}/vinashoes/backend-service:latest
# Check container logs
docker logs test-backend
# Verify API endpoints
curl -f http://localhost:3000/health || echo "Health check failed"
# Cleanup test container
docker stop test-backend && docker rm test-backend
🚀 Next Steps
Chuẩn bị cho Task 9 - ECS Fargate:
Với ECR repository và image đã ready, Task 9 sẽ:
- Tạo ECS Cluster
- Create Task Definition sử dụng ECR image
- Deploy Fargate Service
- Configure load balancing và auto scaling
Quick Verification Command:
# Ensure image is ready for ECS deployment
aws ecr describe-images \
--repository-name vinashoes/backend-service \
--query 'imageDetails[0].[imageTags[0],imageSizeInBytes,imagePushedAt]' \
--output table \
--region ap-southeast-1
🔍 Troubleshooting
Common Issues & Solutions:
-
Authentication Failures:
- Re-run
aws ecr get-login-passwordcommand - Check AWS CLI credentials
- Verify region settings
- Re-run
-
Push Failures:
- Check repository name spelling
- Verify tag format
- Ensure repository exists
-
Scan Failures:
- Wait for scan completion (can take 5-10 minutes)
- Re-trigger scan manually if needed
- Check image format compatibility
-
Permission Denied:
- Verify IAM role policies
- Check ECR resource-based policies
- Ensure proper role assumption
7. Dọn dẹp tài nguyên
7.1. Xóa ECR Repository
AWS CLI Commands:
# List all images in the repository
aws ecr list-images --repository-name vinashoes/backend-service --region ap-southeast-1
# Delete all images in the repository
aws ecr batch-delete-image --repository-name vinashoes/backend-service --image-ids imageTag=latest imageTag=v1.0.0 --region ap-southeast-1
# Delete the repository
aws ecr delete-repository --repository-name vinashoes/backend-service --force --region ap-southeast-1
7.2. Xóa IAM Role
AWS CLI Commands:
# Detach policies from the role
aws iam detach-role-policy --role-name ecsTaskExecutionRole --policy-arn arn:aws:iam::aws:policy/service-role/AmazonECSTaskExecutionRolePolicy
aws iam detach-role-policy --role-name ecsTaskExecutionRole --policy-arn arn:aws:iam::aws:policy/AmazonEC2ContainerRegistryReadOnly
# Delete the role
aws iam delete-role --role-name ecsTaskExecutionRole
7.3. Xóa Lifecycle Policy
AWS CLI Commands:
# Delete lifecycle policy
aws ecr delete-lifecycle-policy --repository-name vinashoes/backend-service --region ap-southeast-1
7.4. Kiểm tra sau khi dọn dẹp
Verification Commands:
# Verify repository deleted
aws ecr describe-repositories --region ap-southeast-1 | grep vinashoes/backend-service || echo "Repository deleted"
# Verify role deleted
aws iam get-role --role-name ecsTaskExecutionRole || echo "Role deleted"
8. Phân tích chi phí
8.1. Bảng giá ECR
| Dịch vụ | Chi phí | Mô tả |
|---|---|---|
| Lưu trữ | $0.10/GB/tháng | Lưu trữ Docker images |
| Transfer dữ liệu | Miễn phí trong region | Transfer trong cùng region ap-southeast-1 |
| Quét lỗ hổng | Miễn phí (Basic) | Quét bảo mật cơ bản |
| Quét nâng cao | $0.09/GB | Quét bảo mật chi tiết (tùy chọn) |
8.2. Phân tích chi phí
Chi phí hàng tháng ước tính:
- Lưu trữ: 5GB images × $0.10 = $0.50/tháng
- Quét bảo mật: Miễn phí
- Transfer: Miễn phí trong region
- Tổng chi phí: $0.50/tháng
8.3. Lợi ích và ROI
Lợi ích của ECR:
- Bảo mật cao: Private registry với encryption
- Tích hợp AWS: Native integration với ECS, Lambda
- Quét lỗ hổng: Tự động phát hiện vulnerabilities
- Lifecycle management: Tự động dọn dẹp images cũ
- High availability: 99.9% uptime SLA
Tính toán ROI:
- Chi phí ECR: $0.50/tháng
- Giá trị tương đương: Docker Hub Pro ($5/tháng) + bảo mật bổ sung
- Tiết kiệm: $4.50/tháng
- ROI: ($4.50 / $0.50) × 100% = 900%
8.4. Giám sát chi phí
AWS Cost Explorer Commands:
# Get ECR costs for last month
aws ce get-cost-and-usage \
--time-period Start=2024-01-01,End=2024-02-01 \
--granularity MONTHLY \
--metrics BlendedCost \
--group-by Type=DIMENSION,Key=SERVICE \
--filter '{
"Dimensions": {
"Key": "SERVICE",
"Values": ["Amazon Elastic Container Registry"]
}
}' \
--region us-east-1
CloudWatch Monitoring:
# Monitor ECR storage usage
aws cloudwatch get-metric-statistics \
--namespace AWS/ECR \
--metric-name RepositorySize \
--dimensions Name=RepositoryName,Value=vinashoes/backend-service \
--start-time 2024-01-01T00:00:00Z \
--end-time 2024-02-01T00:00:00Z \
--period 86400 \
--statistics Maximum \
--region ap-southeast-1
8.5. Chiến lược tối ưu hóa chi phí
Lifecycle Policies:
- Tự động xóa untagged images sau 1 ngày
- Giữ chỉ 10 tagged images gần nhất
- Xóa dev images sau 7 ngày
Image Optimization:
- Sử dụng multi-stage builds để giảm size
- Compress images với tools như docker-slim
- Sử dụng base images nhỏ như alpine
Monitoring & Alerts:
- Set up CloudWatch alarms cho storage usage
- Regular cost reviews với Cost Explorer
- Budget alerts cho ECR spending
📊 Cost Optimization
ECR Pricing Considerations:
- Storage: $0.10 per GB-month
- Data Transfer: Free within same region
- Vulnerability Scanning: Basic (free), Enhanced (additional cost)
Cost Optimization Tips:
- Use lifecycle policies để auto-delete old images
- Regular cleanup của unused images
- Monitor storage usage trong CloudWatch
- Consider image compression techniques